Introduction on the OWASP ZAP Tool
OWASP ZAP :
The OWASP Foundation came online on December 1st 2001 it was established as a not-for-profit charitable organization in the United States on April 21, 2004 to ensure the ongoing availability and support for our work at OWASP.
Why to go for the OWASP ZAP ?
1. Open source Tool
2. Governed by rough consensus & running code
3. Abide by a code of ethics (see ethics)
4. Not-for-profit
5. Not driven by commercial interests
6. Risk based approach
7. Ideal for the Beginers
8. For Automating the Security Test
9. Cross Platforms
10. Easy to Install
11. Internationalized
12. Compatible with Other tools
OWASP ZAP TOP 10 Features :
1. Injection
2. Broken Authentication and Session Management
3. Cross-site Scripting (XSS)
4. Broken Access Control
5. Security Misconfiguration
6. Sensitive Data Exposure
7. Insufficient Attack Protection
8. Cross Site Request Forgery (CSRF)
9. Using Component with known Vulnerabilities
10. Underprotected API’s
Explanation of the Above Features in Details :-
1. Injection
Any source of data can be an injection vector
Often found in SQL,XPATH or NoSQL queries
It occurs when application sends untrusted data to the interpreter
For example, Attacker can execute malicious SQL statements that control a web application's database server.
How to prevent?
Use parameterised queries
Escaping inputs before adding them to the query
Whitelist input validations
2. Broken Authentication and Session Management :-
Authentication details are not protected
Easily guessable credentials
Session IDs in URL
Session IDs don’t time out
Passwords, Session IDs and credentials are sent over unencrypted connections
How to prevent ?
Enforce strong password policies
Restricted number of attempts to login
Session IDs should be random and complicated
Add no cache tags for authentication pages
3. CROSS SITE SCRIPTING
Injects client-side scripts into web pages
Primarily used Javascript
How to prevent?
Sanitisation or validation of user input
Use HttpOnly flag in the HTTP response header
4. BROKEN ACCESS CONTROL
Grant access to functions and contents for specific users
Administrative interfaces that allow site administrators to manage a site over the Internet
How to prevent?
Check access
Get access control matrix
File permissions
Insecure IDs
5. SECURITY MISCONFIGURATION
It arises when security settings are defined, implemented and maintained as defaults/ not set to secure values
Can happen at any level
Platform
Webserver
Application server
Database
Framework
How to prevent?
Disable default accounts and change passwords
Disable/Remove unnecessary files/features
Avoid display of stack-trace to users
Keep software up-to-date
6. SENSITIVE DATA EXPOSURE
When the sensitive information is not adequately protected
Ex: passwords, session tokens, credit card data
Exposing sensitive token in public source code
Old/ weak cryptographic algorithm used
How to prevent?
Don’t store sensitive data
Use strong encryption algorithm
Use of HTTPS on authenticated pages
Set nocache headers to browsers
7. INSUFFICIENT ATTACK PROTECTION (NEW)
No protection against brute force password attacks
No logging of login attempts
No logging of session initiation or completion
Provide quick fixes
8. CROSS SITE REQUEST FORGERY (CSRF)
Forcing the authenticated user to execute unwanted actions on web application
How to prevent?
Use proper CSRF tokens
Avoid simultaneous browsing while logged into an application
9. USING COMPONENTS WITH KNOWN VULNERABILITIES
Component can be OS, CMS, web server, plug-ins or library
How to prevent?
Identify vulnerability in the components that are being used
Upgrade the components to newer versions
10. UNDERPROTECTED APIS
Use of API’s has exploded in modern software to the point that even browser web applications are often written in JS and use API’S to get data.
Client software is easily reversed and communications interpreted.
Testing API’s is similar to testing other web applications
How to prevent
Ensure that you have secured communications between the client and your API
Strong authentication schemes
Implement access control scheme
Protect against injection of all forms
Additional Features Given in ZAP Tool :
1. Auto Tagging
2. Port Scanner
3. Parameter Analysis
4. Smart Card Support
5. Session Comparison
6. Invoke External Application
7. API + Headless mode
8. Dynamic SSL Certificate
9. Anti CSRF Token Handling
This is only the Introduction for the OWASP ZAP Tool.
Now Why we are using this Tool for the Security Test, why not others tools we have used for the Security Testing ?
- Its an open source tool
- We can customize this tool as per our requirement
- It’s a Cross Platform tool - we can install easily in Linux, Mac and Windows
- This tool given the API’s to interact with the Selenium for Automation Security testing.
Note : There are many competitors for the Security testing tools like
Burp Suite Tool
Metasploit
Acunetix
Netsparker
Retina
Now Guy’s will let you know how to install this tool and how to configure the Mozilla Browser with the ZAP Tool.
Steps to be followed for Installation of OWASP ZAP tool in windows tool.
1. Download the zap.exe file and double click on it.
2. You can download the zap tool from this link :-
https://github.com/zaproxy/zaproxy/wiki/Downloads
3. Now install the ZAP tool normally how you install the VLC player or any software in the windows
4. Now once the ZAP tools is installed, open the tool.
5. Note : Before installing ZAP tool, confirm that your system should have Java 7.1 or above
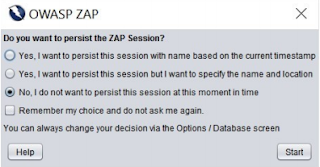
6. When you first start ZAP, you will be asked if you want to persist the ZAP session. By default, ZAP sessions are always recorded to disk in a HSQLDB database with a default name and location. If you do not persist the session, those files are deleted when you exit ZAP. If you choose to persist a session, the session information will be saved in the local database so you can access it later, and you will be able to provide custom names and locations for saving the files.
7. For now, select No, I do not want to persist this session at this moment in time, then click Start. The ZAP sessions will not be persisted for now.
ZAP UI
The ZAP UI is composed of the following elements: 1. Menu Bar – Provides access to many of the automated and manual tools. 2. Toolbar – Includes buttons which provide easy access to most commonly used features. 3. Tree Window – Displays the Sites tree and the Scripts tree. 4. Workspace Window – Displays requests, responses, and scripts and allows you to edit them. 5. Information Window – Displays details of the automated and manual tools. 6. Footer – Displays a summary of the alerts found and the status of the main automated tools.
8. Configure Your Browser to Proxy Through ZAP Before you can begin to run pentests with ZAP, you have to configure your browser to use ZAP as its proxy. By default, ZAP uses: Address: localhost Port: 8080
It’s important to note that, although the self-generated Root CA certificate is uniquely generated for you, it still must be kept private to avoid creating a vulnerability. To export the ZAP Root CA certificate: 1. Start ZAP and click Tools -> Options. 2. On the left pane of the Options window, click Dynamic SSL Certificates. 3. On the right pane, click Save. 4. Select a location to save the certificate to and click Save. Be sure to retain the .cer file extension.
9. To install the ZAP Root CA for Mozilla Firefox:
-Start Firefox and click Preferences.
-On the Advanced tab, click the Encryption tab.
-Click View Certificates.
-On the Trusted root certificates tab, click Import and select the ZAP Root CA file you saved previously.
-In the Import wizard, select Trust this CA to identify web sites.
-Click OK.
10. Try to Connect Your Web Application Once you have configured your browser to use ZAP as its proxy, open your browser and attempt to connect to the web application you are going to test. If you are unable to reach your web application, check the following:
- Verify the proxy settings the browser is using to connect to ZAP.
- Verify the proxy settings in ZAP are those the browser is using to try to connect to ZAP.
- Verify the web application you want to test is running.
- Check to see whether your network requires a proxy to reach your web application. If so, you may need to configure ZAP to use a proxy. To configure ZAP to use an outgoing proxy:
- Start ZAP and on the Menu Bar, click Tools -> Options.
- Select Connection in the left pane.
- In the use proxy chain section of the Connection settings, check the Use an outgoing proxy server checkbox.
- Enter the Address/Domain Name and Port for your network proxy.
- Click OK to save the settings and verify that you can now connect to your web application. -- Once your browser can successfully connect to your web application, you are ready to run a test.
Reporting And Analysis :-
- Generate detailed Vulnerabilities report
- Reports available in the HTML, XML, JSON formats.
- Graphical Representation for easy interpretation
- And Install all the plugins from the OWASP Zap Tool.
Post author by QA Nishant Paul


Thanks Shiv
ReplyDeleteThanks for time to read and sharing your comments.
DeletePretty article! I found some useful information in your blog, it was awesome to read, thanks for sharing this great content to my vision, keep sharing. Need to learn
ReplyDeleteSecurity Testing Services
Test Automation Services
Software Testing Services
Compatibility Testing Services
Regression Testing Services
Very valuable information shared in this blog . I was looking for something like that and found it here.
ReplyDeleteTop QA Companies
Top Automation Testing Companies
Top Mobile App Testing Companies
Top Performance Testing Companies
Thanks for Sharing Information to us. If Someone wants to know about Top Software testing Companies this is the Right place for you!
ReplyDeleteInformative content about security testing tools. Really helpful to know the detailed information about the tools and how it will helps testing purpose. This tools helps security testing services companies for best product output.
ReplyDelete